利用openVuln API自动化查询思科产品漏洞
利用openVuln API自动化查询思科产品漏洞
B站视频链接:https://www.bilibili.com/video/BV1ZG411P7cf/?spm_id_from=333.999.0.0
微信公众号:自刘地

一、背景
安全自动化是目前一个比较热门的话题,网络安全问题往往是由软件自身的安全漏洞被利用导致,所以及时修复已知安全漏洞,是抵御网络攻击非常重要的一环。这个文档介绍一下,如何利用思科openVuln API,自动化的查询特定思科产品的安全漏洞,并且通过Excel的方式展现这些漏洞信息。
先看一下最后代码输出的Excel截图,代码可以根据提供的软件版本、CVE编号、产品名称来查询漏洞信息,每次查询的漏洞信息会存储为一个CSV文件,最后将所有的CSV信息合并到一个Excel文件中,每个Excel Sheet就是一个CSV文件中的信息,Excel列宽会根据内容自动调整。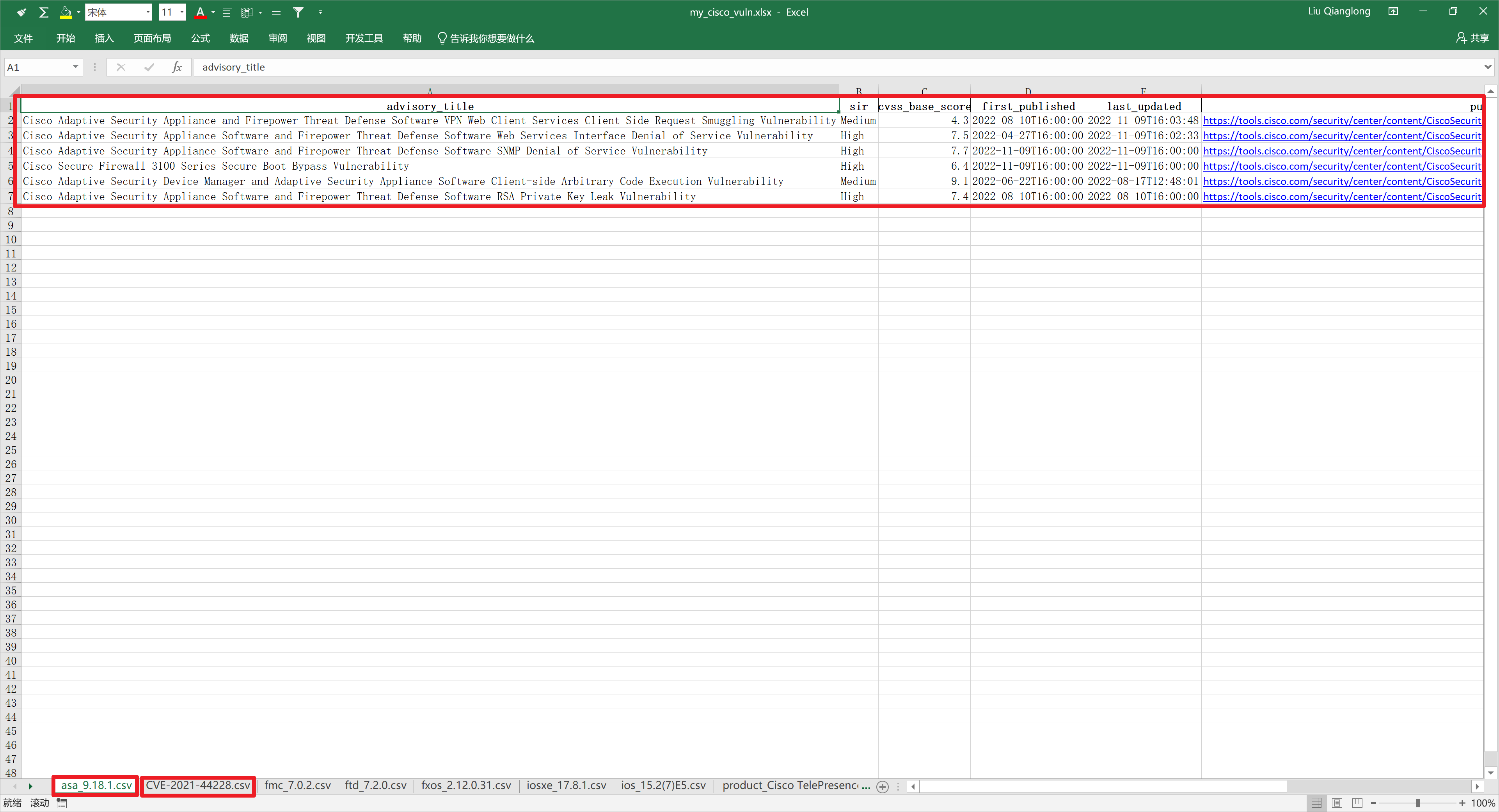
除了利用API的方式查询,另外也可以通过思科提供的图形化界面来查询漏洞信息,可以登录https://tools.cisco.com/security/center/publicationListing.x网站查询思科设备的漏洞信息。
也可以查询特定版本的漏洞信息,链接:https://tools.cisco.com/security/center/softwarechecker.x
例如这里查询IOS 15.2(7)E2的漏洞信息。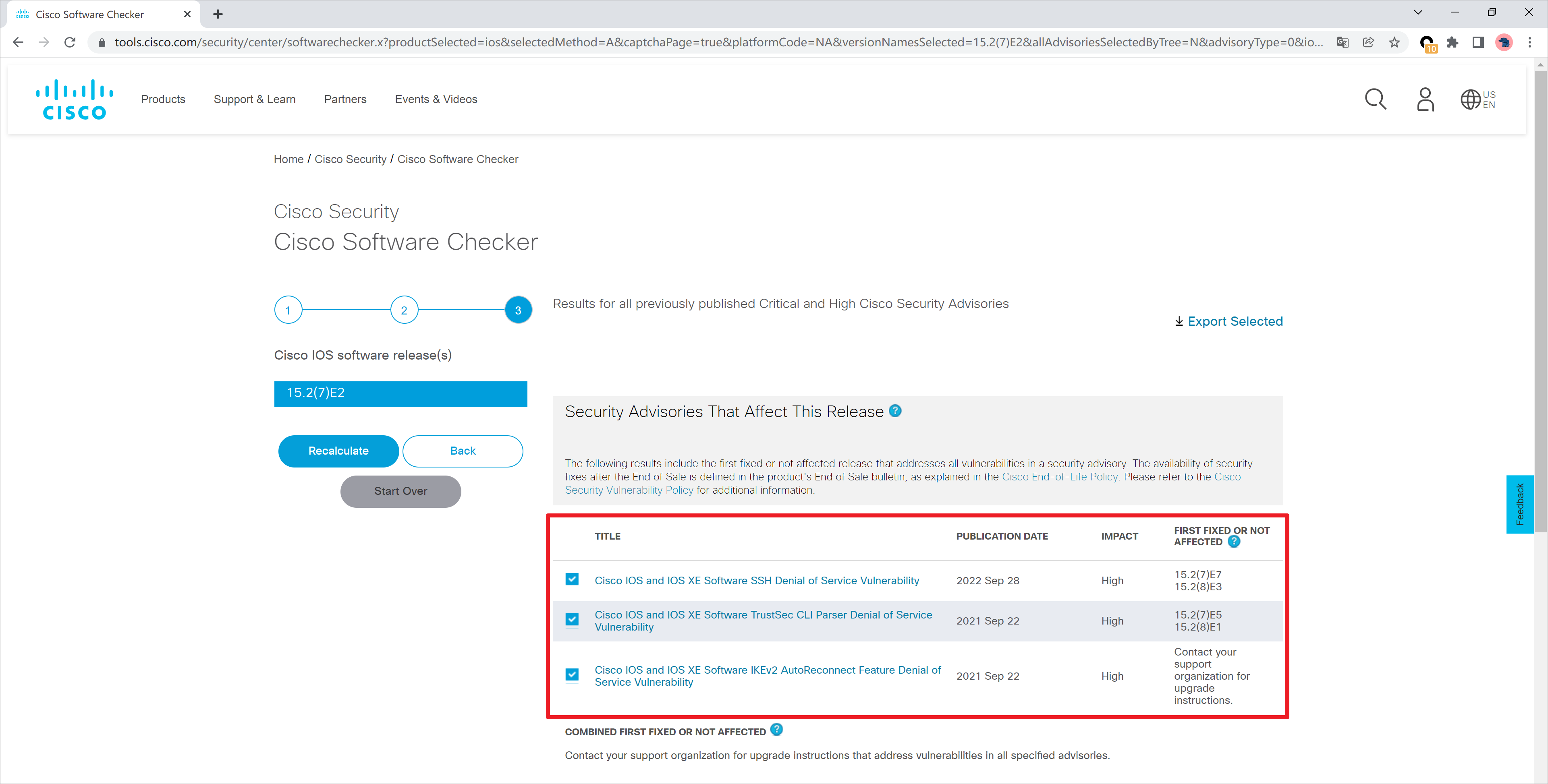
二、Cisco PSIRT openVuln API 简介
思科产品安全事件响应小组(Cisco Product Security Incident Response Team,PSIRT)是一个专门的全球团队,负责接收、调查和公开报告与思科产品和网络有关的安全漏洞信息 [1]。
思科PSIRT团队提供了openVuln API[2],允许用户查询思科产品的漏洞信息,漏洞信息支持多种格式的行业安全标准:
CVE:通用漏洞枚举(Common Vulnerability Enumeration),它就像是所有公开漏洞的字典表,对已公开的漏洞进行统一编号。由Mitre公司(非盈利机构)建立与维护,网址:https://cve.org/
CWE:常见弱点枚举 (Common Weakness Enumeration) 是MITRE公司继CVE之后的又一个安全漏洞词典,主要针对开发社区和安全从业人员社区,列出了架构、设计、代码或实施中可能出现的常见软件和硬件弱点,这些弱点可能导致可利用的安全漏洞 [3] ,网址:https://cwe.mitre.org
CVSS:通用漏洞评分系统 (Common Vulnerability Scoring System) 提供了一种评估漏洞严重性的方法,企业在修复漏洞时,可以根据这个优先级来修复。CVSS现在的版本是V3.1,漏洞评分为0
10分,漏洞分为4个等级:`LOW(0.13.9)、MEDIUM(4.06.9)8.9)、HIGH(7.0、CRITICAL(9.0~10.0)` [4],网址:https://first.org/cvssCSAF:通用安全咨询框架 (Common Security Advisory Framework) 是结构化机器可读漏洞相关咨询的规范。CSAF 是通用漏洞报告框架 (CVRF) 的新名称和替代品。网址:https://csaf.io/
三、获取思科openVuln API访问凭证
思科openVuln API使用OAuth2进行认证,所以需要认证获得授权之后才能查询。
登录思科网站,创建凭证信息,网址https://apiconsole.cisco.com/apps/myapps
创建一个应用名称,选择OAuth2.0的凭证类型,这里我选择客户端凭证。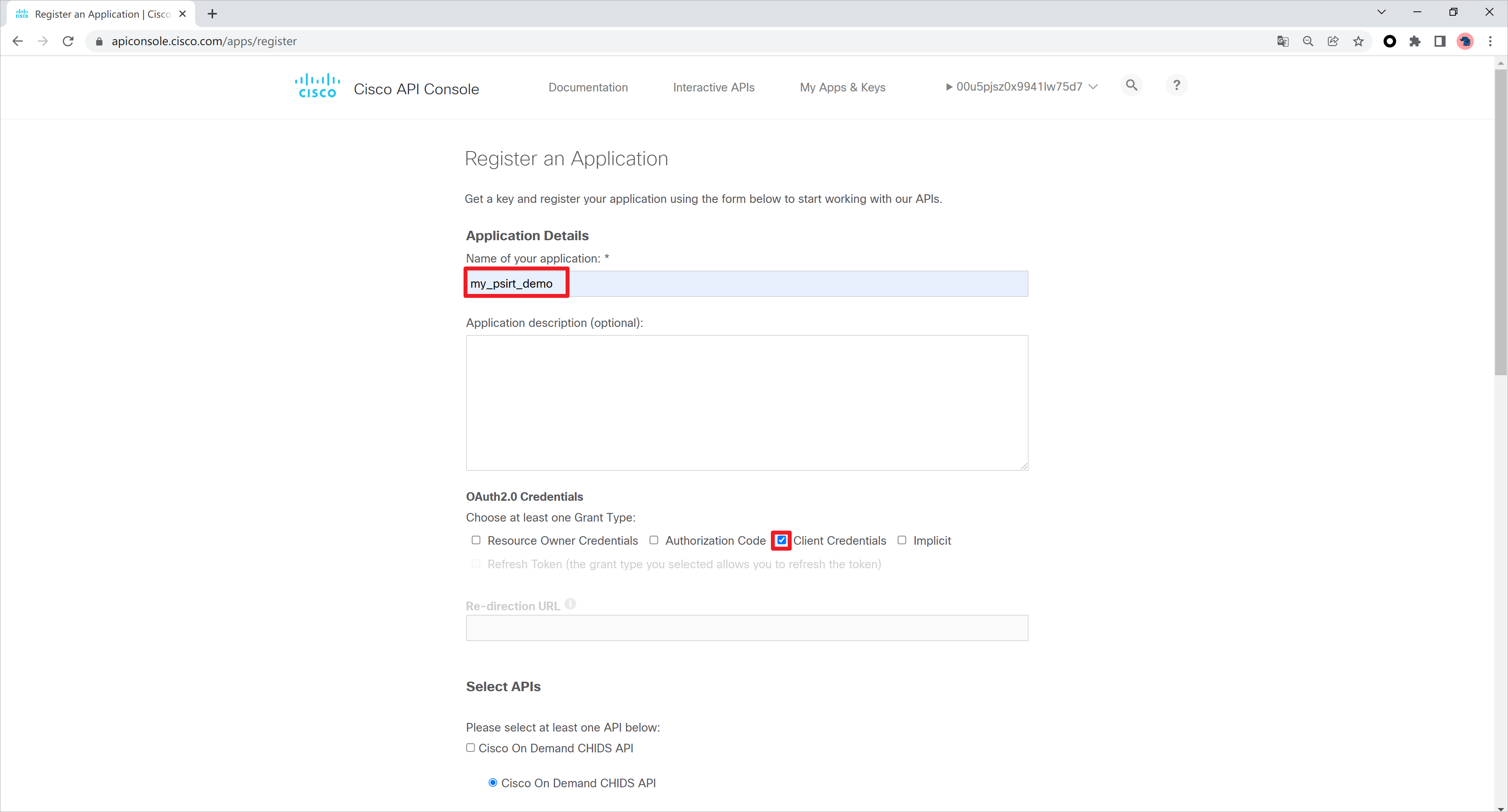
勾选Cisco PSIRT openVuln API的权限,注意这个API的速率限制,每秒5次请求,每分钟30次请求。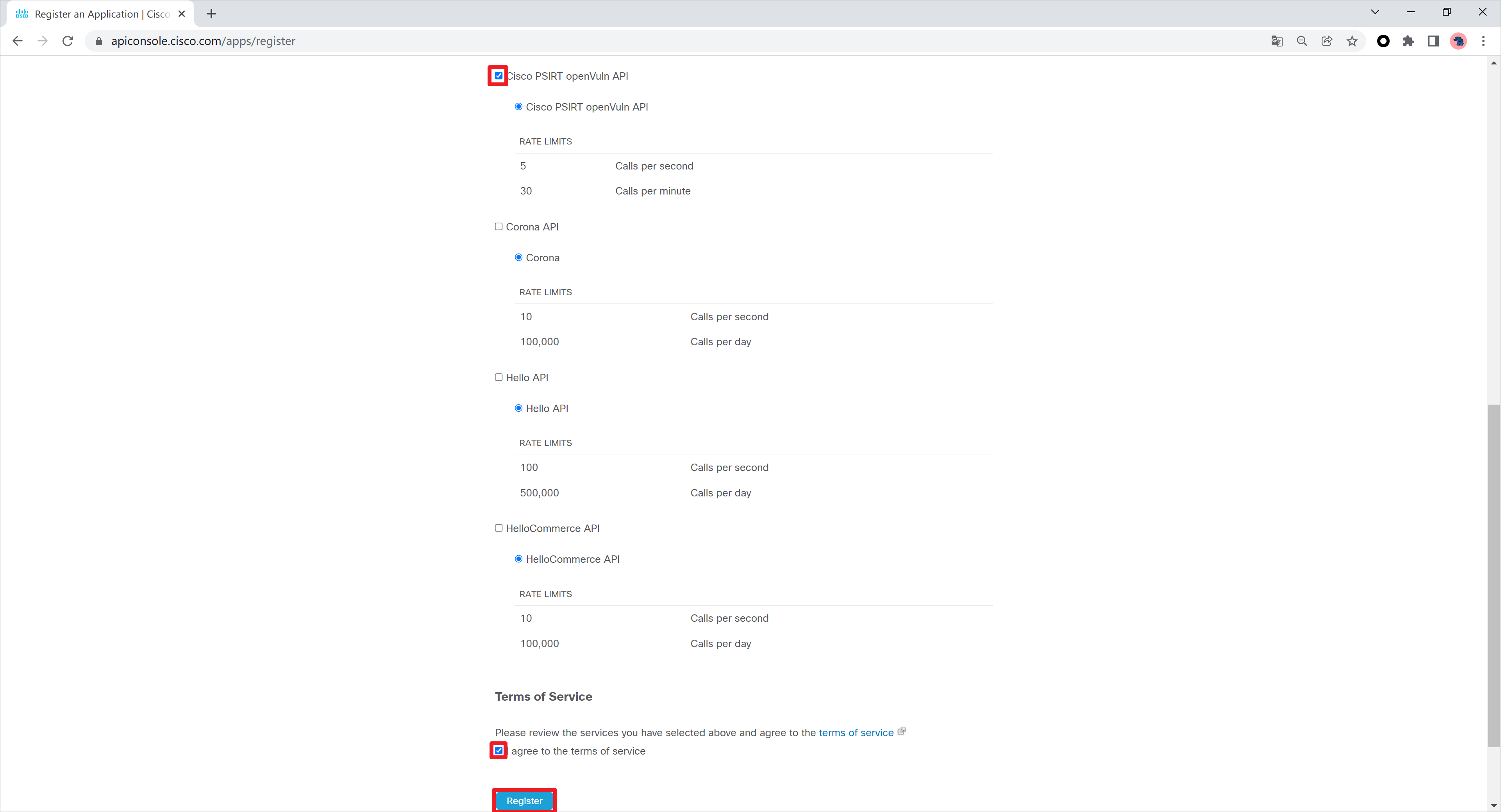
创建完成。
查看产生的凭证信息,记录这个信息,KEY:djshucbvmpu4cmcsgufwt36w,CLIENT SECRET:TVJxz72ADUBKdb7ySjTzzcQp,注意不要泄露这个凭证信息(我会在演示完后销毁这个凭证)。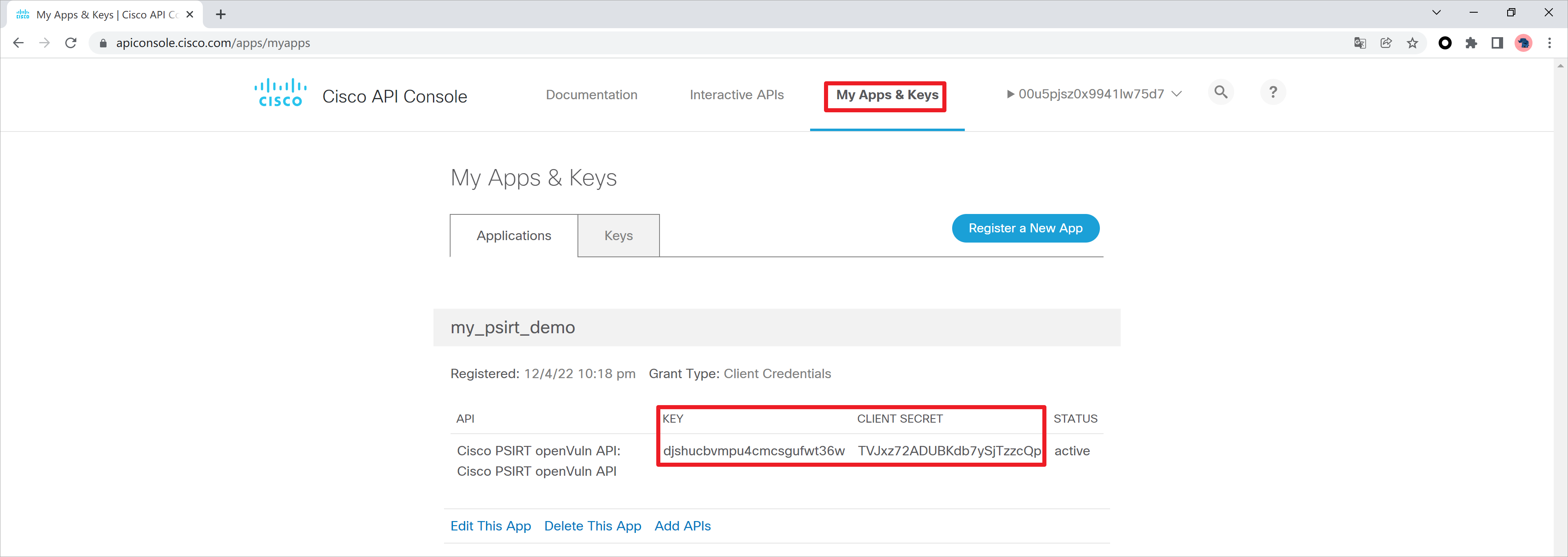
四、测试访问openVuln API
4.1 通过Postman软件测试
在Postman软件中选择配置OAuth 2.0的凭证信息,设置Token名称,设置凭证类型为Client Credentials,令牌URL为https://cloudsso.cisco.com/as/token.oauth2,Client ID为djshucbvmpu4cmcsgufwt36w,Client Secret:TVJxz72ADUBKdb7ySjTzzcQp,填写完信息之后,点击产生新的Token信息,然后使用这个Token。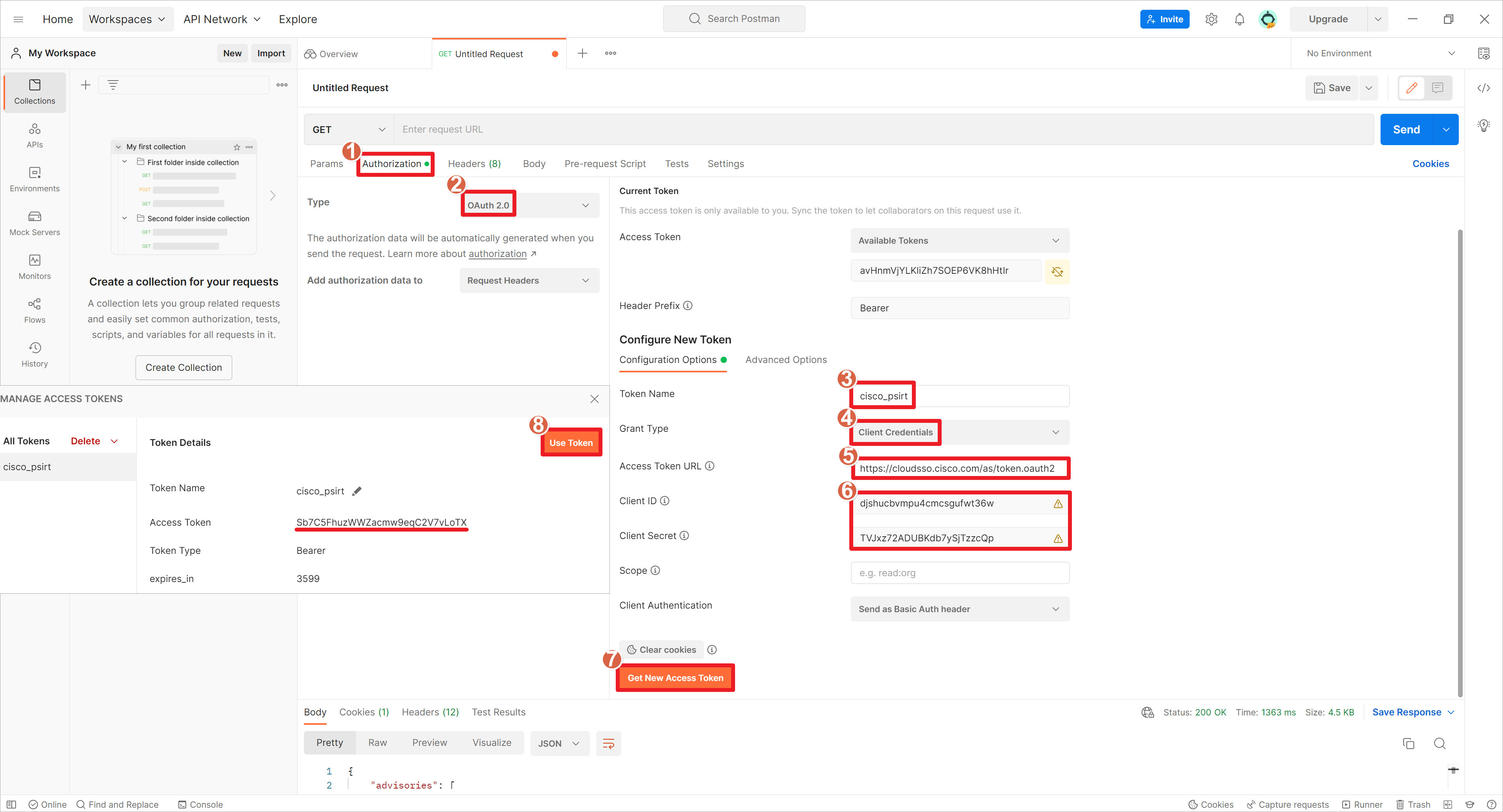
在软件中发起HTTP GET请求,通过CVE信息查询受影响的产品 [5],HTTP GET测试URL为:https://api.cisco.com/security/advisories/v2/cve/CVE-2021-44228
4.2 通过Terminal运行测试
通过pip3 install openVulnQuery安装openVulnQuery模块 [6]后,可以在Linux terminal使用命令行测试。
1 | [root@centos8 ~]# pip3 install openVulnQuery |
安装之后创建一个凭证文件,输入CLIENT_ID和CLIENT_SECRET信息。
也可以将这个凭证信息配置在环境变量中,例如:export CLIENT_ID="djshucbvmpu4cmcsgufwt36w",export CLIENT_SECRET="TVJxz72ADUBKdb7ySjTzzcQp"。
1 | [root@centos8 ~]# vim Credentials.json |
调用凭证信息,查询2022年8月份所有critical级别的漏洞。
1 | [root@centos8 ~]# openVulnQuery --config Credentials.json --severity critical --first_published 2022-08-01:2022-08-30 |
4.3 将OpenVulnQuery做为库(Library)测试
创建一个python测试脚本,填入client_id和client_secret。这里查询特IOS 15.2(7)E5这个版本漏洞信息。
1 | [root@centos8 ~]# vim prist_demo.py |
下面是所有可以获取的字段信息,可以根据需求自行过滤。
1 | advisory_id |
运行测试脚本的输出信息。
1 | [root@centos8 ~]# python3 prist_demo.py |
五、Python最终代码
5.1 使用openVulnQuery API 2.0
思科PSIRT在2022年8月1日发布了新的API接口,并通告旧的API接口将会下线。但是目前通过pip install安装的Python库使用的是旧API接口,如果想要在Python代码中使用新的API接口,可以在pip install安装模块后,从Github下载最新的代码,替换整个_library目录中的所有内容。下面演示一下这个过程。
首先正常安装openVulnQuery模块。
1 | [root@centos8 ~]# pip3 install openVulnQuery |
安装之后,查询openVulnQuery模块的安装目录。
1 | [root@centos8 _library]# find / -name "advisory.py" |
可以查看目录中的config.py文件,关注最后一行的API_URL信息,新的API_URL链接为:API_URL = "https://api.cisco.com/security/advisories/v2"。所以可以确认通过pip install安装的模块,使用的是旧的API接口。
1 | [root@centos8 _library]# more /usr/local/lib64/python3.6/site-packages/openVulnQuery/_library/config.py |
从Github下载最新的代码。
1 | [root@centos8 ~]# git clone https://github.com/CiscoPSIRT/openVulnQuery.git |
将Github中_library目录的所有文件拷贝到原有的_library目录中,并覆盖原有文件。
1 | cp -r /root/openVulnQuery/openVulnQuery/_library/ /usr/local/lib64/python3.6/site-packages/openVulnQuery/ |
5.2 Python查询思路
这个代码的主要目的是:根据提供的软件版本、CVE编号、产品名称来查询漏洞信息,并将所有漏洞信息整合到Excel中。
首先是根据什么信息来查询漏洞,最准确的是根据系统加版本来查询,可以明确的获取当前版本的所有漏洞信息。但是可惜的是,并不是所有思科产品都支持这个查询方式,只有下面这些系统可以通过软件版本的方式查询。
1 | Cisco IOS Software (ios) |
其他不支持软件版本方式查询的系统,可以通过产品名称来查询,例如WLC、ISE等。如果你想了解产品的全称,可以访问https://tools.cisco.com/security/center/productBoxData.x?prodType=CISCO获取思科的所有产品名称。
通过CVE编号查询受影响的产品,也是一个比较实用的查询方式。例如最近突发了一个Log4j2漏洞,已知CVE编号是CVE-2021-44228,想了解有哪些思科产品受到影响,可以通过这种方式来查询,列出所有受到影响的产品。
查询完成后,就是用什么样的格式来输出这些信息。我将每个查询的结果生成一个CSV文件,因为CSV是一个纯文本文件,所以可以直接使用文本编辑器查看。但是如果查询很多产品的漏洞后,想在一个文件中查看,Excel是更加合适的格式。Excel可以将每个CSV文件作为一个Sheet,这样查看起来更加清晰。所有代码最终会输出两类文件,一类是基于每次查询产生的CSV文件,一个是所有CSV合并起来的Excel文件。另外将CSV合并到Excel时,默认列的宽度默认较小,可以根据列的内容动态的来调整Excel列宽,这样可读性更好。
5.3 Python 最终代码
创建一个文件夹,用于存放查询结果的CSV文件。
1 | [root@centos8 ~]# mkdir cisco_vuln_csv_folder |
安装这次代码所需的Python模块pandas,openpyxl,XlsxWriter,openVulnQuery。
注意openVulnQuery模块已经在5.1部分替换了最新的代码文件,使用了API 2.0接口。
1 | [root@centos8 ~]# pip3 install pandas openpyxl XlsxWriter |
创建Python代码文件,请自行替换client_id和client_secret。处于安全性考虑,账号信息可以放到另外的配置文件中来调用,这里为了简化代码,我直接放在源文件中了。另外这个代码也有很多重复性的部分可以优化,这里只是给大家提供一个思路,可以根据需要自行修改。如果有想要更好的查询方式,也欢迎联系我 :)
1 | import csv |
运行代码测试。
1 | [root@centos8 ~]# python3 cisco_psirt_vuln.py |
查看输出的CSV文件和Excel文件。
1 | [root@centos8 ~]# ls cisco_vuln_csv_folder/ |
打开Excel文件查看,通过软件版本方式的查询结果是非常准确的,对应的软件版本一定有这些漏洞。
通过产品名称的方式查询,会返回这个产品已知的所有漏洞信息,需要人工进一步的去判断,所关注的版本是否收到影响。不过可以根据first_publishded字段查看漏洞的发布时间,如果当前运行的版本是2020年发布的,那么也没有必要查看之前时间发布的漏洞。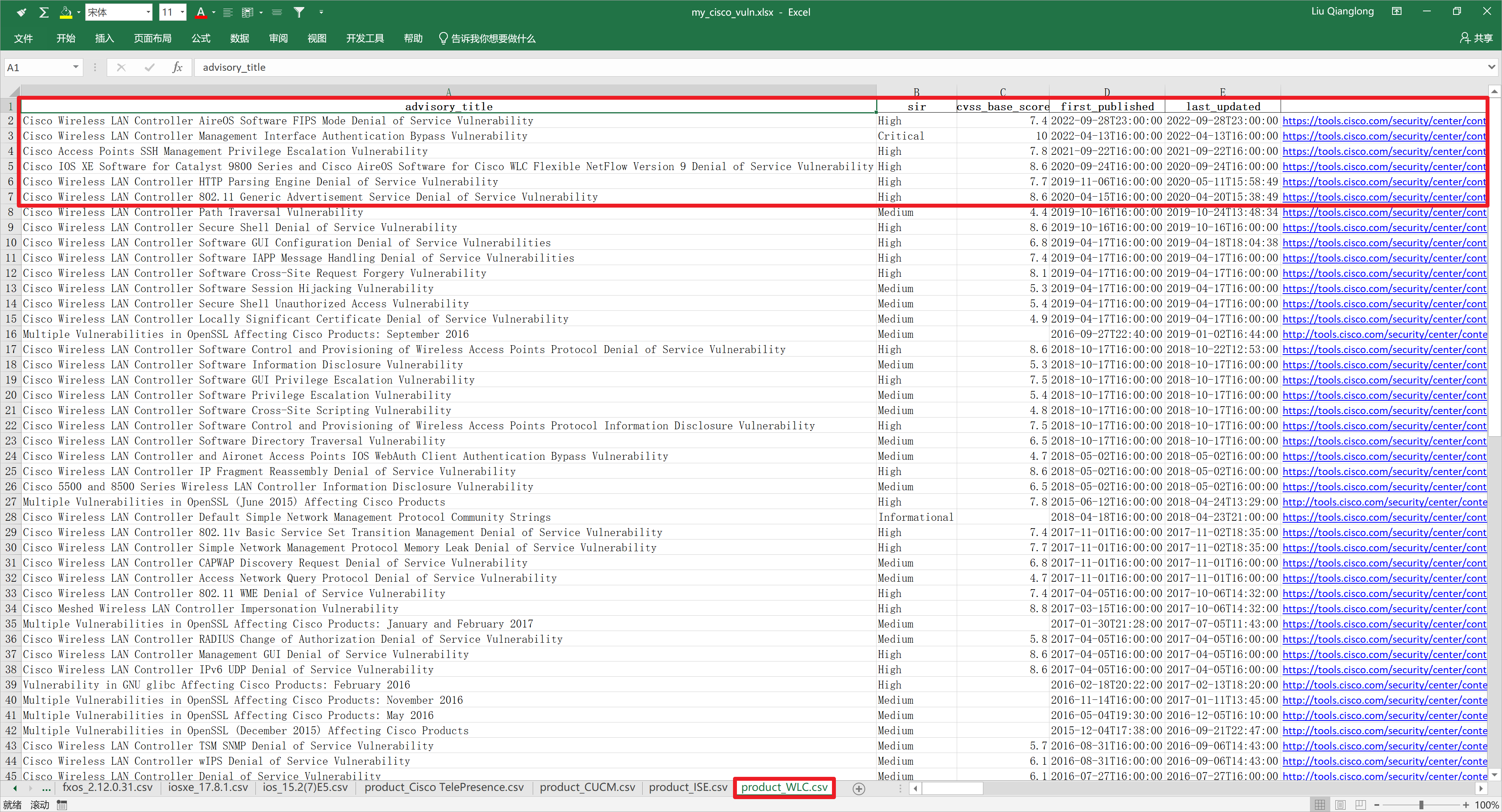
六、运行代码可能遇见的报错
当未安装XlsxWriter模块时会遇见下面报错,可以通过安装这个模块解决,pip3 install XlsxWriter
1 | [root@centos8 ~]# python3 cisco_psirt_vuln.py |
如果使用了旧的API,可能遇见下面报错。因为通过pip install安装的openVulnQuery模块,使用的是旧的API,其中没有get_by_asa这个方法。解决方法参考5.1部分,使用最新的Github代码,代码链接https://github.com/CiscoPSIRT/openVulnQuery
1 | [root@centos8 ~]# python3 cisco_psirt_vuln.py |
当网络不稳定,或者API超过限制速率时,可能遇见下面报错。可以尝试更换主机的网络环境,或者等1分钟后再测试。API速率限制是每秒5次请求,每分钟30次请求。
1 | requests.exceptions.ConnectionError: HTTPSConnectionPool(host='cloudsso.cisco.com', port=443): Max retries exceeded with url: /as/token.oauth2?client_id=djshucbvmpu4cmcsgufwt36w&client_secret=TVJxz72ADUBKdb7ySjTzzcQp (Caused by NewConnectionError('<urllib3.connection.VerifiedHTTPSConnection object at 0x7fc2bcea1c88>: Failed to establish a new connection: [Errno 101] Network is unreachable',)) |
七、参考文档
- [1] Cisco Product Security Incident Response Team:https://www.cisco.com/c/dam/en_us/about/doing_business/trust-center/docs/cisco-psirt-infographic.pdf
- [2] PSIRT openVuln API:https://developer.cisco.com/docs/psirt/#!overview/overview
- [3] 道高一丈,且看CWE4.2的新特性:https://zhuanlan.zhihu.com/p/340011094
- [4] 揭开CVSS的神秘面纱:https://codeant.valiantsec.cn/industry_detail?id=8042e0c9345c46efbe182698150f84a9
- [5] Cisco PSIRT openVuln API Query by CVE ID:https://developer.cisco.com/docs/psirt/#!api-reference/query-by-cve-id
- [6] Github CiscoPSIRT/openVulnQuery https://github.com/CiscoPSIRT/openVulnQuery