ISP Failover PAT配置
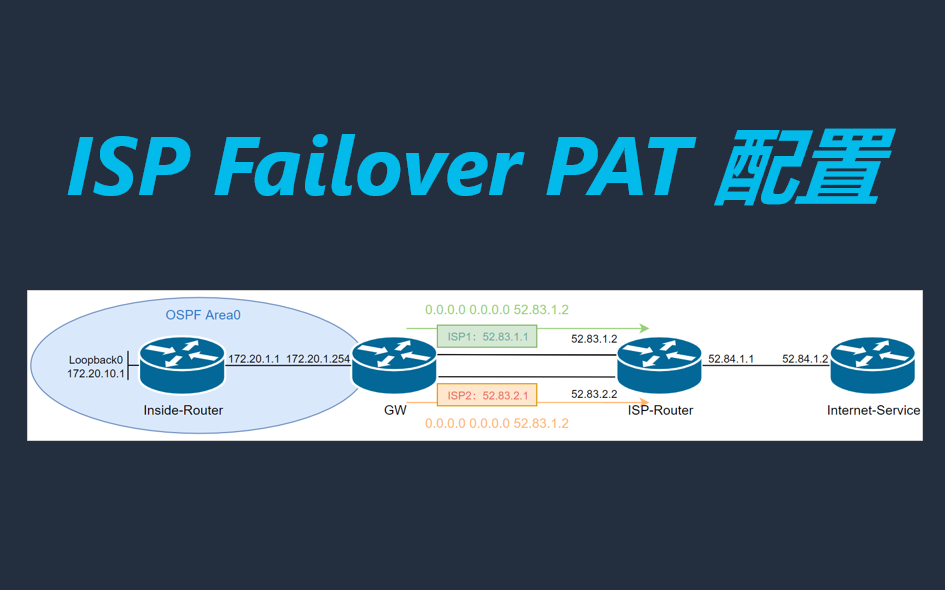
1、介绍
为了实现出口ISP链路的冗余,可以在出口路由器上连接两条不同的ISP线路,获得链路冗余的同时也带来新的问题,即如何决定流量送往哪个ISP。一般来说有两种流量选择方式:负载均衡和主备切换。
负载均衡:出口网关配置两条默认路由分别到ISP1和ISP2,去往ISP的流量会通过这两条等价的默认路由进行负载均衡,可以通过ip cef load-sharing algorithm命令修改负载均衡的算法,参见文档。负载均衡方式的优势在于更加充分的利用两条线路带宽,当其中一个ISP不可用时,故障切换速度更快。
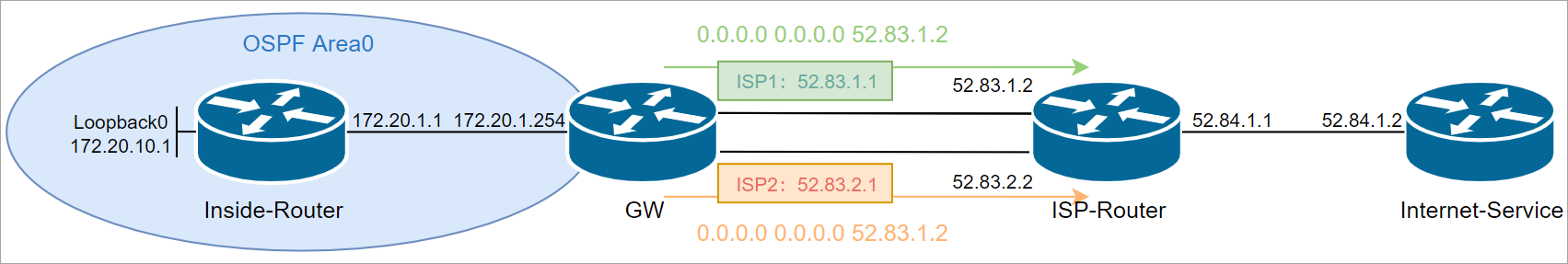
主备切换:利用浮动静态路由和SLA结合来实现主用到ISP1,当ISP1出现故障时能自动切换到ISP2。主备切换的优势在于出口公网IP固定,线路更加稳定。但是备用链路的带宽长期是闲置的。当主用ISP1可用时,流量不会走备用ISP2,但是你可以通过添加明细路由到ISP2改变流量选路,也可以通过PRB抓取特定的源IP地址通过备用ISP2出去。
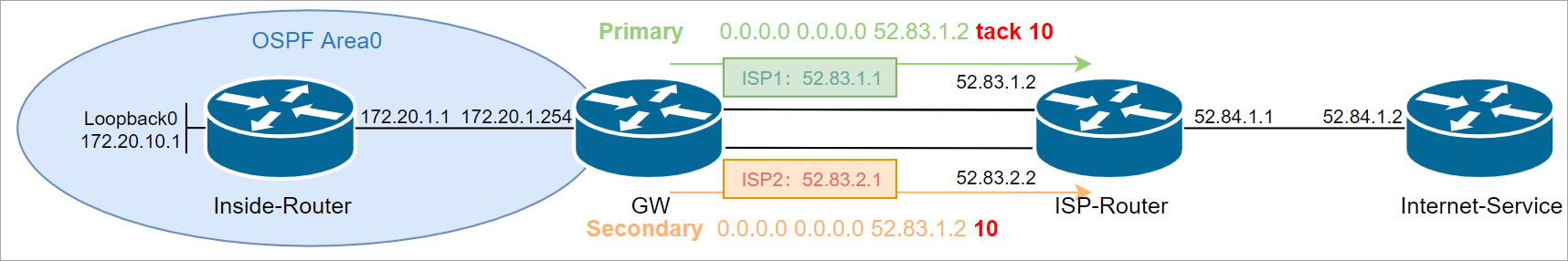
另外需要注意的是这种NAT的切换需要结合route-map来配置。
2、拓扑图
这里使用EVE-NG的CSR1Kv搭建的实验环境,使用GNS3和其他型号路由器对实验结果没有影响。
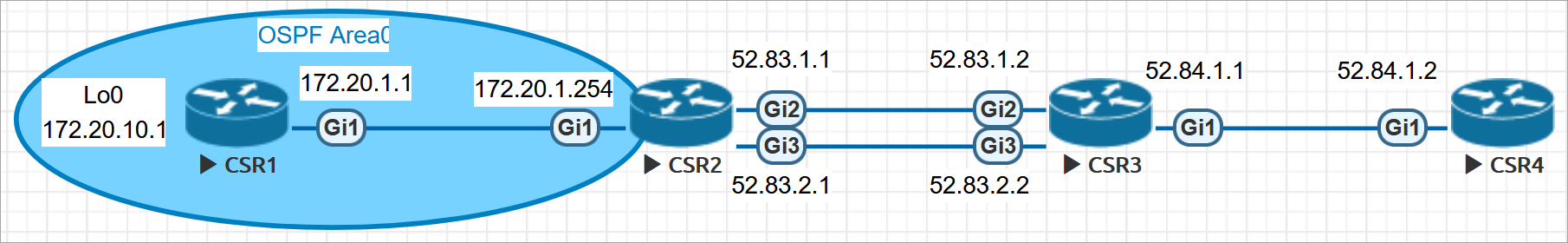
3、设备初始化
这里初始化所有设置的IP地址,以及内部路由配置,出口网关的路由和NAT在下一个部分配置。
- CSR1(Inside-Router)
host Inside-Router
!
interface Loopback0
ip address 172.20.10.1 255.255.255.0
!
interface GigabitEthernet1
ip address 172.20.1.1 255.255.255.0
!
router ospf 10
network 172.20.1.0 0.0.0.255 area 0
network 172.20.10.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 172.20.1.254
- CSR2(GW)
host GW
!
interface GigabitEthernet1
ip address 172.20.1.254 255.255.255.0
!
interface GigabitEthernet2
ip address 52.83.1.1 255.255.255.0
!
interface GigabitEthernet3
ip address 52.83.2.1 255.255.255.0
!
router ospf 10
network 172.20.1.0 0.0.0.255 area 0
- CSR3(ISP-Router)
host ISP-Router
!
interface GigabitEthernet1
ip address 52.84.1.1 255.255.255.0
!
interface GigabitEthernet2
ip address 52.83.1.2 255.255.255.0
!
interface GigabitEthernet3
ip address 52.83.2.2 255.255.255.0
- CSR4(ISP-Service)
host ISP-Service
!
interface GigabitEthernet1
ip address 52.84.1.2 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 52.84.1.1
4、负载均衡配置
这里配置去往ISP1和ISP2的默认路由为等价路由,需要利用route-map来结合NAT进行配置。

- CSR1(Inside-Router)
interface GigabitEthernet1
ip address 172.20.1.254 255.255.255.0
ip nat inside
!
interface GigabitEthernet2
ip address 52.83.1.1 255.255.255.0
ip nat outside
!
interface GigabitEthernet3
ip address 52.83.2.1 255.255.255.0
ip nat outside
ip access-list extended NAT_ACL
permit ip 172.20.0.0 0.0.255.255 any log
!
route-map NAT_ISP1 permit 10
match ip address NAT_ACL
match interface GigabitEthernet2
!
route-map NAT_ISP2 permit 10
match ip address NAT_ACL
match interface GigabitEthernet3
ip nat pool ISP1_Pool 52.83.1.100 52.83.1.110 netmask 255.255.255.0
ip nat pool ISP2_Pool 52.83.2.100 52.83.2.110 netmask 255.255.255.0
ip nat inside source route-map NAT_ISP1 pool ISP1_Pool overload
ip nat inside source route-map NAT_ISP2 pool ISP2_Pool overload
ip route 0.0.0.0 0.0.0.0 52.83.1.2
ip route 0.0.0.0 0.0.0.0 52.83.2.2
- 查看网关的出口路由,去往ISP1和ISP2的等价路由。
GW#show ip route
S* 0.0.0.0/0 [1/0] via 52.83.2.2
[1/0] via 52.83.1.2
O 172.20.10.1/32 [110/2] via 172.20.1.1, 1d02h, GigabitEthernet1
- 内部路由器测试
Inside-Router#ping 52.84.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
.!!!!
Inside-Router#ping 52.84.1.2 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
Packet sent with a source address of 172.20.10.1
.!!!!
- 查看转换表项,可以看到不同的源IP从不同的ISP链路出去。
GW#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 52.83.2.100:1 172.20.10.1:48 52.84.1.2:48 52.84.1.2:1
icmp 52.83.1.100:1 172.20.1.1:47 52.84.1.2:47 52.84.1.2:1
Total number of translations: 2
- 通过
show ip cef exact-route命令可以用来预测源到目的IP使用的下一跳接口和IP地址。
GW#show ip cef exact-route 172.20.1.1 52.84.1.2
172.20.1.1 -> 52.84.1.2 =>IP adj out of GigabitEthernet2, addr 52.83.1.2
GW#show ip cef exact-route 172.20.10.1 52.84.1.2
172.20.10.1 -> 52.84.1.2 =>IP adj out of GigabitEthernet3, addr 52.83.2.2
5、主备配置
5.1、主备切换
这里配置ISP1为主用,利用SLA监控ISP1直连地址,当ISP1不可用时路由切换到ISP2上。

- CSR2(GW),注意这里为了试验需要将sla的参数调的更小了,生产环境下需要自己设计这个参数。
frequency表示这里每3秒发送一次探针,timeout表示发送探针后1秒后还未接受到那么认为这个探针超时了,threshold表示连续两次超时后达到阈值。所以结合上面的参数,当52.83.1.2不可达后,最多需要6秒sla会达到阈值。(注意,这里需要先删除上面指向ISP2的路由之后再添加管理距离更大的路由)
ip sla 10
icmp-echo 52.83.1.2 source-ip 52.83.1.1
threshold 2
timeout 1000
frequency 3
ip sla schedule 10 life forever start-time now
track 10 ip sla 10 reachability
no ip route 0.0.0.0 0.0.0.0 52.83.1.2
ip route 0.0.0.0 0.0.0.0 52.83.1.2 track 10
ip route 0.0.0.0 0.0.0.0 52.83.2.2 10
- GW查看路由表和SLA状态
GW#show ip route
S* 0.0.0.0/0 [1/0] via 52.83.1.2
GW#show ip sla summary
IPSLAs Latest Operation Summary
Codes: * active, ^ inactive, ~ pending
ID Type Destination Stats Return Last
(ms) Code Run
-----------------------------------------------------------------------
*10 icmp-echo 52.83.1.2 RTT=12 Over thresh 0 seconds ago
old
- 内部路由器ping测试
Inside-Router#ping 52.84.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
.!!!!
Inside-Router#ping 52.84.1.2 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
Packet sent with a source address of 172.20.10.1
.!!!!
- GW查看转换表项,可以看到流量都是从ISP1出去。
GW#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 52.83.1.100:1 172.20.1.1:49 52.84.1.2:49 52.84.1.2:1
icmp 52.83.1.100:2 172.20.10.1:50 52.84.1.2:50 52.84.1.2:2
Total number of translations: 2
- CSR3(ISP-Router),关闭G2端口,模拟ISP1故障。
ISP-Router(config)#interface g2
ISP-Router(config-if)#shutdown
- GW上查看sla状态变为Down,默认路由切换到了ISP2上。
*Jun 16 07:53:00.039: %TRACK-6-STATE: 10 ip sla 10 reachability Up -> Down
GW#show ip route
S* 0.0.0.0/0 [1/0] via 52.83.2.2
- Inside-Router重新发起流量测试
Inside-Router#ping 52.84.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 13/18/34 ms
Inside-Router#ping 52.84.1.2 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
Packet sent with a source address of 172.20.10.1
!!!!!
- GW查看NAT转换表项,流量都从ISP2出去。
GW#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 52.83.2.100:2 172.20.10.1:55 52.84.1.2:55 52.84.1.2:2
icmp 52.83.2.100:1 172.20.1.1:54 52.84.1.2:54 52.84.1.2:1
Total number of translations: 2
5.2、使用明细路由控制出口ISP
在上面的主备切换模式下,所有流量都通过ISP1出去,如果你需要指定去往某些特定IP的地址从ISP2出去,可以通过配置明细路由来实现。
- 恢复ISP-Router G2号接口
ISP-Router(config)#int g2
ISP-Router(config-if)#no shutdown
- 去往52.84.1.2/32的地址通过ISP2访问。
GW(config)#ip route 52.84.1.2 255.255.255.255 52.83.2.2
- 在Inside路由器上ping测试到52.84.1.1和52.84.1.2
Inside-Router#ping 52.84.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/12/18 ms
Inside-Router#ping 52.84.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 13/20/46 ms
- 查看转换表项,看到去往52.84.1.2通过ISP2出去
GW#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 52.83.1.100:1 172.20.1.1:58 52.84.1.1:58 52.84.1.1:1
icmp 52.83.2.100:1 172.20.1.1:59 52.84.1.2:59 52.84.1.2:1
Total number of translations: 2
5.3、使用PBR控制出口ISP
如果是希望控制特定的源IP地址从ISP2出去,那么通过添加明细路由就无法解决这个问题了,这种场景下可以通过PBR(策略路由)来实现这个需求,通过抓取指定的源IP地址送到ISP2的下一跳出去。
- 删除添加的明细路由,重新回到主备状态。
GW(config)#no ip route 52.84.1.2 255.255.255.255 52.83.2.2
- CSR2(GW),配置PRB,抓取Inside-Router的环回口从ISP2出去。
ip access-list extended TO_ISP2_ACL
permit ip host 172.20.10.1 any
route-map Route_ISP2 permit 10
match ip address TO_ISP2_ACL
set ip next-hop 52.83.2.2
interface GigabitEthernet1
ip address 172.20.1.254 255.255.255.0
ip policy route-map Route_ISP2
- 在Insid-Router上使用不用的源IP进行测试
Inside-Router#ping 52.84.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 13/19/26 ms
Inside-Router#ping 52.84.1.2 source lo 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 52.84.1.2, timeout is 2 seconds:
Packet sent with a source address of 172.20.10.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 12/23/53 ms
- 查看转换表项,确认Inside-Router环回口地址从ISP2出去。
GW#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 52.83.1.100:1 172.20.1.1:63 52.84.1.2:63 52.84.1.2:1
icmp 52.83.2.100:1 172.20.10.1:62 52.84.1.2:62 52.84.1.2:1
Total number of translations: 2
上述的PRB配置有一个隐患,因为PRB下一跳强制指向了ISP2的接口,如果ISP2不可达了,那么抓取的源IP无法进行切换。可以在PRB也结合SLA配置来实现自动切换。
- 配置SLA监控ISP2接口地址,PBR调用SLA。
ip sla 20
icmp-echo 52.83.2.2 source-ip 52.83.2.1
threshold 2
timeout 1000
frequency 3
ip sla schedule 20 life forever start-time now
track 20 ip sla 20 reachability
GW(config)#route-map Route_ISP2 permit 10
GW(config-route-map)#no set ip next-hop 223.70.229.53 52.83.2.2
GW(config-route-map)#set ip next-hop verify-availability 52.83.2.2 1 track 20
- 在Inside-Router上进行长ping测试
Inside-Router#ping 52.84.1.2 source lo 0 re 1000000
- 关闭ISP-Router的G3接口,模拟ISP2故障
ISP-Router(config)#int g3
ISP-Router(config-if)#shutdown
- 如果为Inside-Router持续ping时,GW会认为是一个连续的会话,会继续匹配以前的NAT转换表项,从而刷新NAT转换表项(默认超时时间60s)造成不通。
GW#show ip nat translations verbose
Pro Inside global Inside local Outside local Outside global
icmp 52.83.1.100:1 172.20.10.1:67 52.84.1.2:67 52.84.1.2:1
create: 06/16/21 10:18:21, use: 06/16/21 10:18:21, timeout: 00:00:56
Map-Id(In): 12
Appl type: none
Mac-Address: 0000.0000.0000 Input-IDB: GigabitEthernet1
entry-id: 0xe94efa80, use_count:1
- 此时需要强制清空NAT转换表项即可。或者Inside-Router重新发起一次ping也可以正常通信,因为新的ping进行会在GW上创建新的NAT转换表项。
GW#cle ip nat translation *
5.4、PAT地址池
在实际环境中ISP提供公网地址时,互联地址和公网IP地址池可能不在一个网段。例如互联地址段是52.83.1.0/24,提供的公网地址池是52.83.100.100~52.83.100.110,在这个实验环境下模拟这个场景时需要在ISP-Router上添加去往52.83.100.0/24的路由即可。
- GW 修改地址池
no ip nat pool ISP1_Pool 52.83.1.100 52.83.1.110 netmask 255.255.255.0
no ip nat pool ISP2_Pool 52.83.2.100 52.83.2.110 netmask 255.255.255.0
ip nat pool ISP1_Pool 52.83.100.100 52.83.100.110 netmask 255.255.255.0
ip nat pool ISP2_Pool 52.83.200.100 52.83.200.110 netmask 255.255.255.0
- ISP-Router添加去往NAT地址池的路由即可
ip route 52.83.100.0 255.255.255.0 52.83.1.1
ip route 52.83.200.0 255.255.255.0 52.83.2.1
参考文档
- ISP Failover with Default Routes using IP SLA Tracking:https://www.cisco.com/c/en/us/support/docs/ip/ip-routing/200785-ISP-Failover-with-default-routes-using-I.html
- CONFIGURING POLICY-BASED ROUTING (PBR) WITH IP SLA TRACKING - AUTO REDIRECTING TRAFFIC:http://www.firewall.cx/cisco-technical-knowledgebase/cisco-routers/861-cisco-router-pbr-ipsla-auto-redirect.html
- Cisco IP SLA — Using a Cisco Router to generate traffic:https://www.practicalnetworking.net/stand-alone/cisco-ip-sla-using-a-cisco-router-to-generate-traffic/

